Which two configuration elements can be used to prevent abuse of stolen credentials? (Choose two.)
Which Palo Alto Networks pre-sales tool involves approximately 4 hour interview to discuss a customer's current security posture?
Which option is required to Activate/Retrieve a Device Management License on the M-100 Appliance after the Auth Codes have been activated on the Palo Alto Networks Support Site?
Which proprietary technology solutions will allow a customer to identify and control traffic sources regardless of internet protocol (IP) address or network segment?
What will best enhance security of a production online system while minimizing the impact for the existing network?
Which component is needed for a large-scale deployment of NGFWs with multiple Panorama Management Servers?
XYZ Corporation has a legacy environment with asymmetric routing. The customer understands that Palo Alto Networks firewalls can support asymmetric routing with redundancy. Which two features must be enabled to meet the customer's requirements? (Choose two.)
What are two benefits of using Panorama for a customer who is deploying virtual firewalls to secure data center traffic? (Choose two.)
Which three items contain information about Command-and-Control (C2) hosts? (Choose three.)
Which two configuration items are required when the NGFW needs to act as a decryption broker for multiple transparent bridge security chains? (Choose two.)
Which four actions can be configured in an Anti-Spyware profile to address command-and-control traffic from compromised hosts? (Choose four.)
Which CLI command will allow you to view latency, jitter and packet loss on a virtual SD-WAN interface?
A)
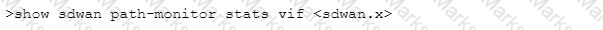
B)
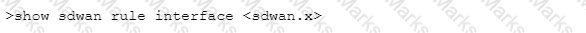
C)
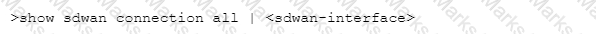
D)

What are three sources of malware sample data for the Threat Intelligence Cloud? (Choose three)
A prospective customer currently uses a firewall that provides only Layer 4
inspection and protections. The customer sees traffic going to an external destination, port 53, but cannot determine what Layer 7 application traffic is going over that port
Which capability of PAN-OS would address the customer's lack of visibility?
Which three considerations should be made prior to installing a decryption policy on the NGFW? (Choose three.)
Select the BOM for the Prisma Access, to provide access for 5500 mobile users and 10 remote locations (100Mbps each) for one year, including Base Support and minimal logging. The customer already has 4x PA5220r 8x PA3220,1x Panorama VM for 25 devices.
Which three categories are identified as best practices in the Best Practice Assessment tool? (Choose three.)
Which domain permissions are required by the User-ID Agent for WMI Authentication on a Windows Server? (Choose three.)
An administrator wants to justify the expense of a second Panorama appliance for HA of the management layer.
The customer already has multiple M-100s set up as a log collector group. What are two valid reasons for deploying Panorama in High Availability? (Choose two.)
What helps avoid split brain in active / passive high availability (HA) pair deployment?
What is an advantage of having WildFire machine learning (ML) capability Inline on the firewall?
Which three actions should be taken before deploying a firewall evaluation unt in a customer environment? (Choose three.)
A client chooses to not block uncategorized websites.
Which two additions should be made to help provide some protection? (Choose two.)
When HTTP header logging is enabled on a URL Filtering profile, which attribute-value can be logged?
Which three features are used to prevent abuse of stolen credentials? (Choose three.)
A potential customer requires an NGFW solution which enables high-throughput, low-latency network security, all while incorporating unprecedented features and technology. They need a solution that solves the performance problems that plague today's security infrastructure.
Which aspect of the Palo Alto Networks NGFW capabilities can you highlight to help them address the requirements?
In which two cases should the Hardware offering of Panorama be chosen over the Virtual Offering? (Choose two.)
The firewall includes predefined reports, custom reports can be built for specific data and actionable tasks, or predefined and custom reports can be combined to compile information needed to monitor network security.
The firewall provides which three types of reports? (Choose three.)
What are two core values of the Palo Alto Network Security Operating Platform? (Choose two.}
A Fortune 500 customer has expressed interest in purchasing WildFire; however, they do not want to send discovered malware outside of their network.
Which version of WildFire will meet this customer’s requirements?