In addition to creating a Security policy, how can an AI Access Security be used to prevent users from uploading financial information to ChatGPT?
When a review of devices discovered by IoT Security reveals network routers appearing multiple times with different IP addresses, which configuration will address the issue by showing only unique devices?
An engineer configures a Security policy for traffic originating at branch locations in the Remote Networks configuration scope. After committing the configuration and reviewing the logs, the branch traffic is not matching the Security policy.
Which statement explains the branch traffic behavior?
Which feature will fetch user and group information to verify whether a group from the Cloud Identity Engine is present on a security processing node (SPN)?
What will cause a connector to fail to establish a connection with the cloud gateway during the deployment of a new ZTNA Connector in a data center?
Which statement is valid in relation to certificates used for GlobalProtect and pre-logon?
During a deployment of Prisma Access (Managed by Strata Cloud Manager) for mobile users, a SAML authentication type and authentication profile in the Cloud Identity Engine application is successfully created.
Using this SAML authentication, what is a valid next step to configure authentication for mobile users?
Which two actions can a company with Prisma Access deployed take to use the Egress IP API to automate policy rule updates when the IP addresses used by Prisma Access change? (Choose two.)
A customer is implementing Prisma Access (Managed by Strata Cloud Manager) to connect mobile users, branch locations, and business-to- business (B2B) partners to their data centers.
The solution must meet these requirements:
The mobile users must have internet filtering, data center connectivity, and remote site connectivity to the branch locations.
The branch locations must have internet filtering and data center connectivity.
The B2B partner connections must only have access to specific data center internally developed applications running on non-standard ports.
The security team must have access to manage the mobile user and access to branch locations.
The network team must have access to manage only the partner access.
Which two options will allow the engineer to support the requirements? (Choose two.)
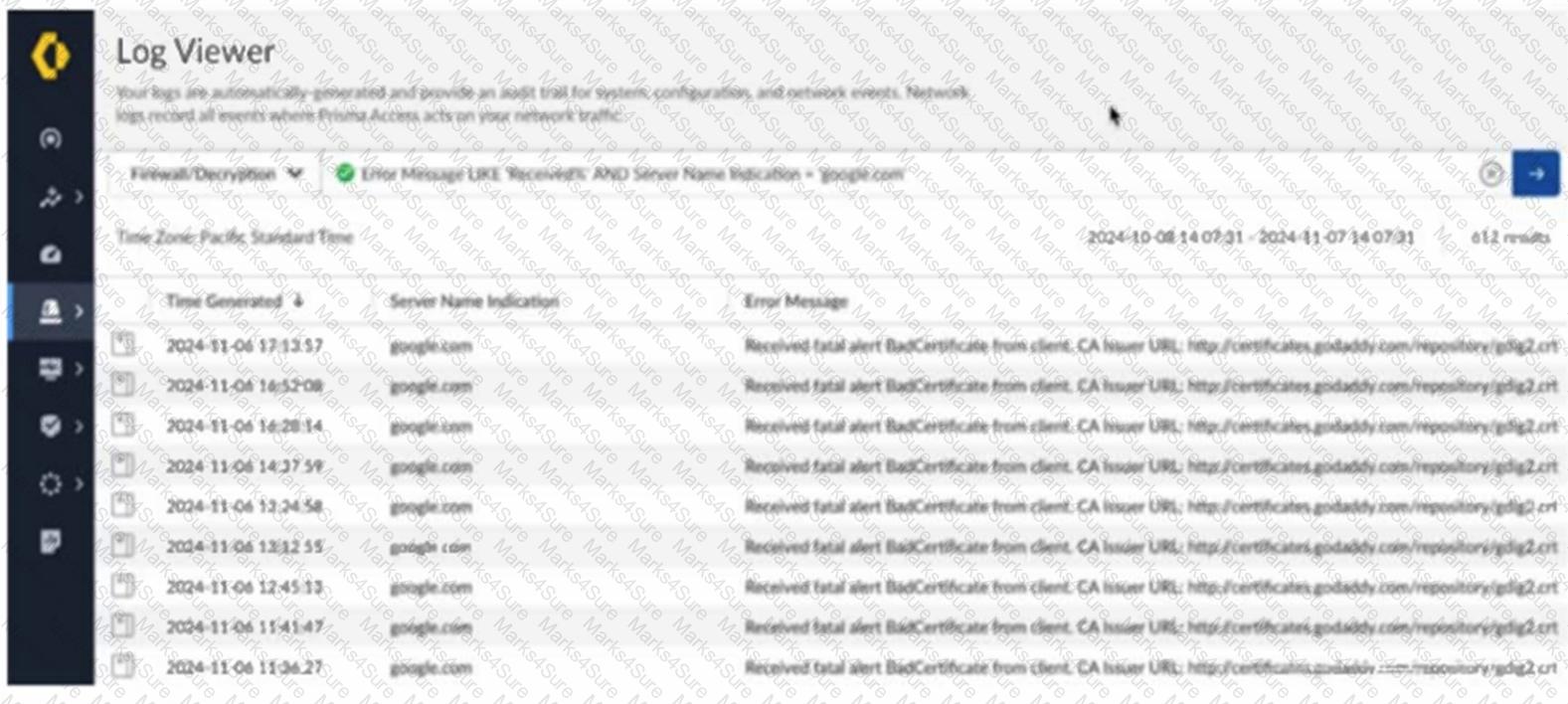
Based on the image below, which two statements describe the reason and action required to resolve the errors? (Choose two.)
When using the traffic replication feature in Prisma Access, where is the mirrored traffic directed for analysis?
A large retailer has deployed all of its stores with the same IP address subnet. An engineer is onboarding these stores as Remote Networks in Prisma Access. While onboarding each store, the engineer selects the “Overlapping Subnets” checkbox.
Which Remote Network flow is supported after onboarding in this scenario?